Iam Team Process Diagram Tips For Getting Iam Implementation
Open source tools for identity and access management Iam maturity pathmaker toward navigate organization Workflow architecture workflows oim request provisioning approval oracle identity governance figure description manual docs cd
How Graphs Solve Two Biggest Problems of Traditional IAM Systems
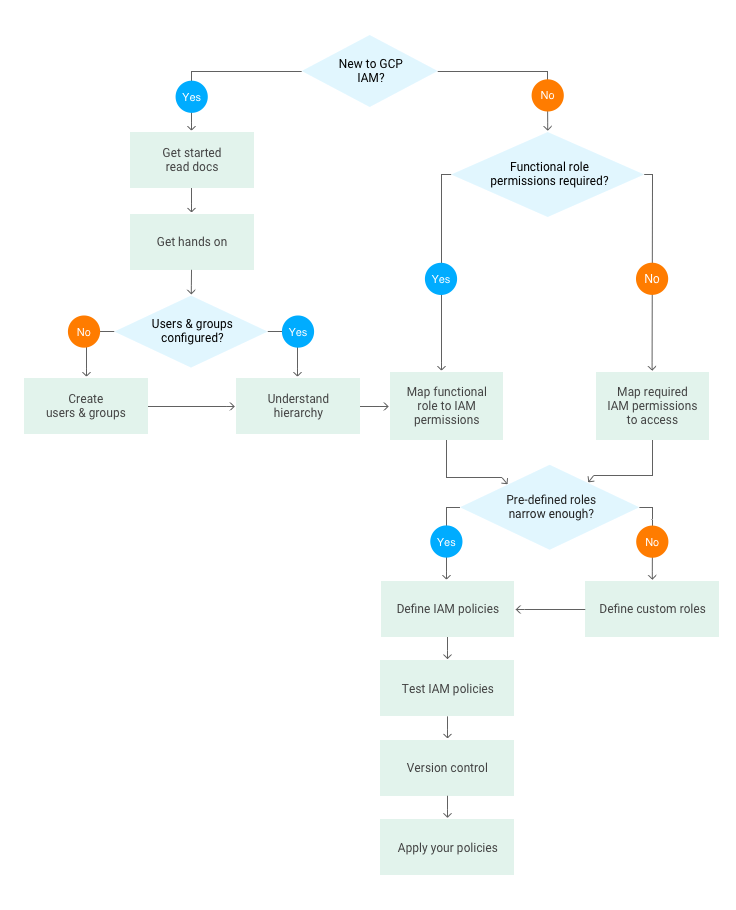
Iam framework process contextualized mafraq Standard iam business processes: corporate / intranet deployment Google cloud platform blog: getting to know cloud iam
Iam vs pam
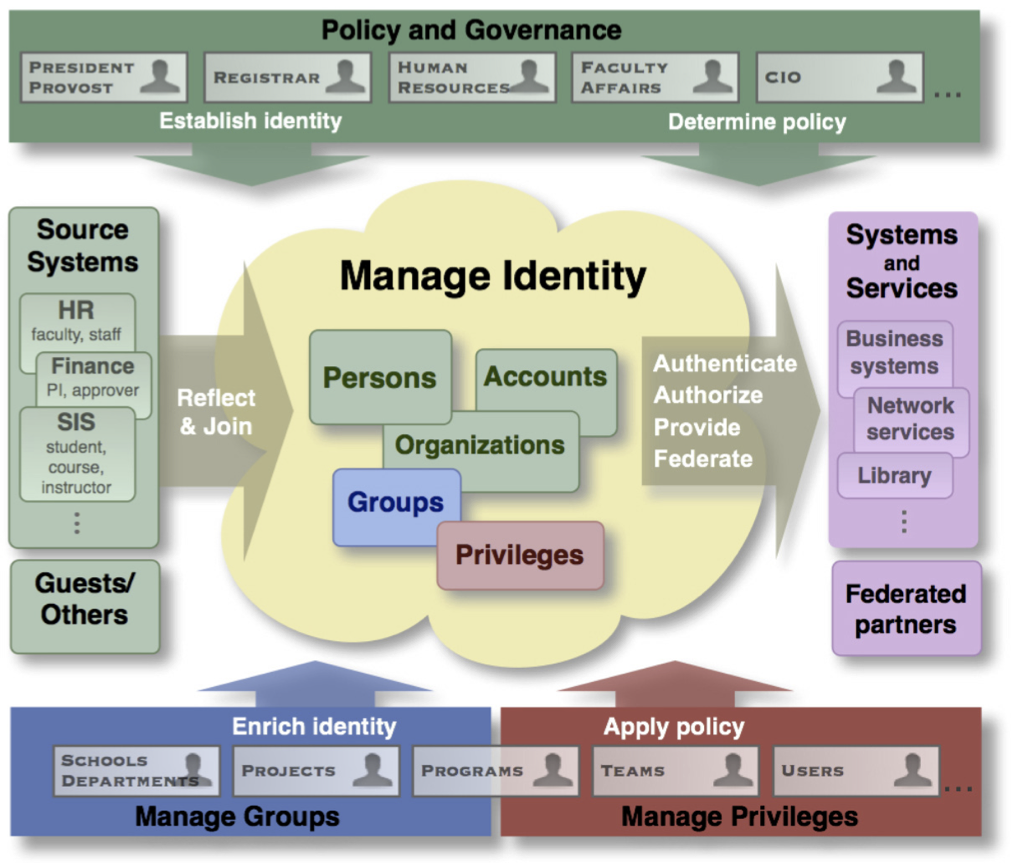
Identity and access management controlsIdentity and access management : iam architecture and practice Flowchart of iam algorithm. doi:10.1371/journal.pone.0130814.g002Understanding key identity & access management components.
Iam implementing approaches five integratingIam savanti Introduction to process designerIam overview.

Identity and access management (iam)
Iam : iam meditation amma mata amritanandamayi devi _ empowering peopleIam (identity and access management) & active directory environments Iam processesTips for getting iam implementation right.
What is identity management (id management) ?Iam security – pathmaker group Iam idproHow graphs solve two biggest problems of traditional iam systems.

Iam flowchart drill
How to centralize and automate iam policy creation in sandboxArchitecture – linux on fire Iam policy aws security sandbox environments test development architecture figure solution centralize automate creation amazonDeeper thoughts on modernizing iam.
Iam policy diagram overview io definitionAccess diagram at terry westfall blog Developing workflows for approval and manual provisioningManagement identity access iam cycle life diagram flow tools source open user steps sequence.

How to create an effective iam program
Iam cloud getting know google organization hierarchical gcp various example resources theirProject team organization chart template Overall flowchart of the model building process. iam: intravenousSoftware: identity access manager iam.
Aws — iam overview. what is aws identity and access…Five approaches to consider when implementing iam The iam process phases and steps. the level of model- and...Process iam workflow diagram actors introduction designer based ibm.

Iam identity premise sap softguide
Iam access identity management computer communication diagram belowContextualized iam framework used for introducing the iam process to Iam identity efecte 100mmComputer and communication: identity and access management (iam).
Getting to know cloud iamIam management identity components service technology definition protection unstructured vital brings four contains pieces many Iam business challenges traditional enterprise single operational approaches overcoming processes corporate standard slideshare deployment sign.